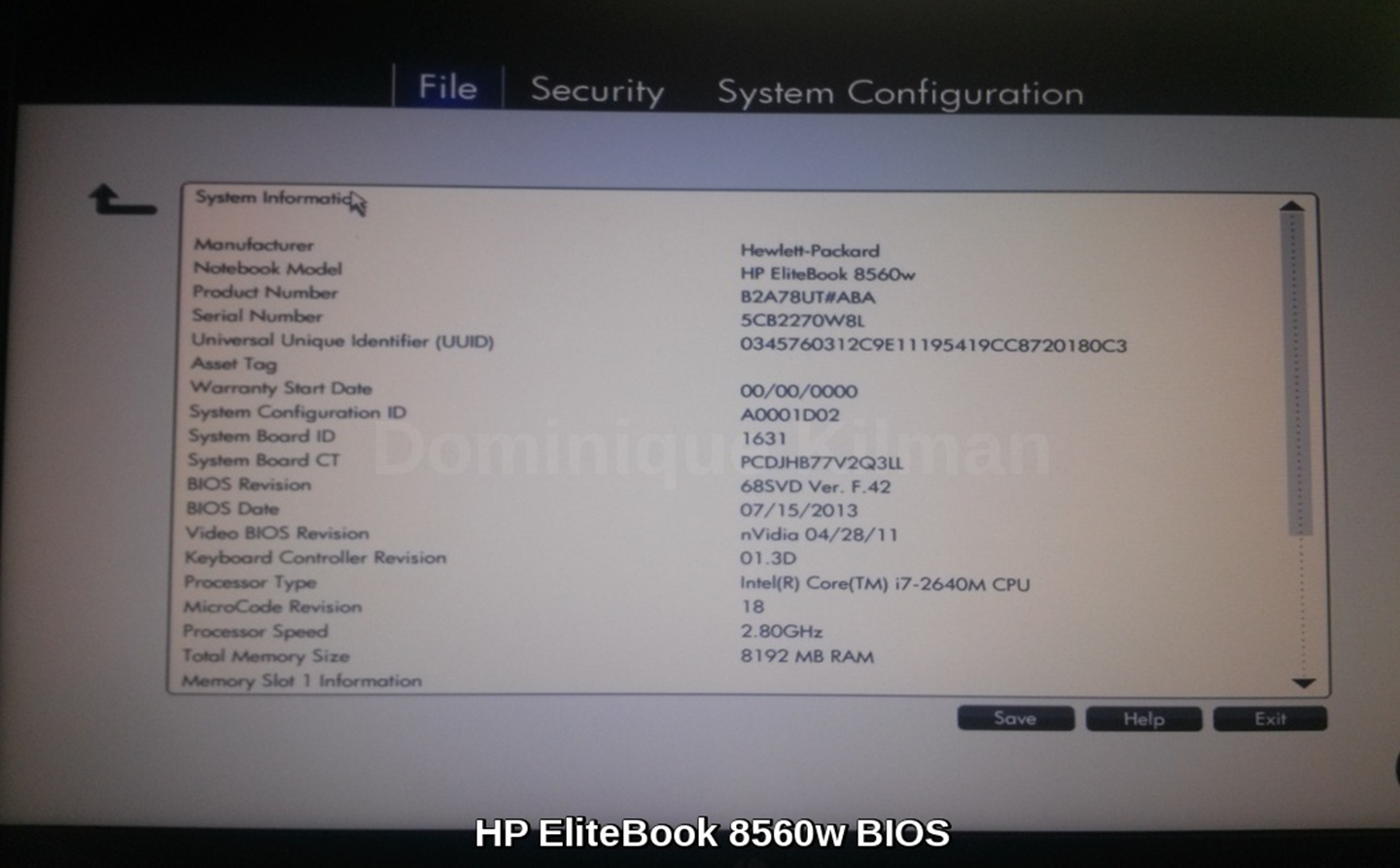
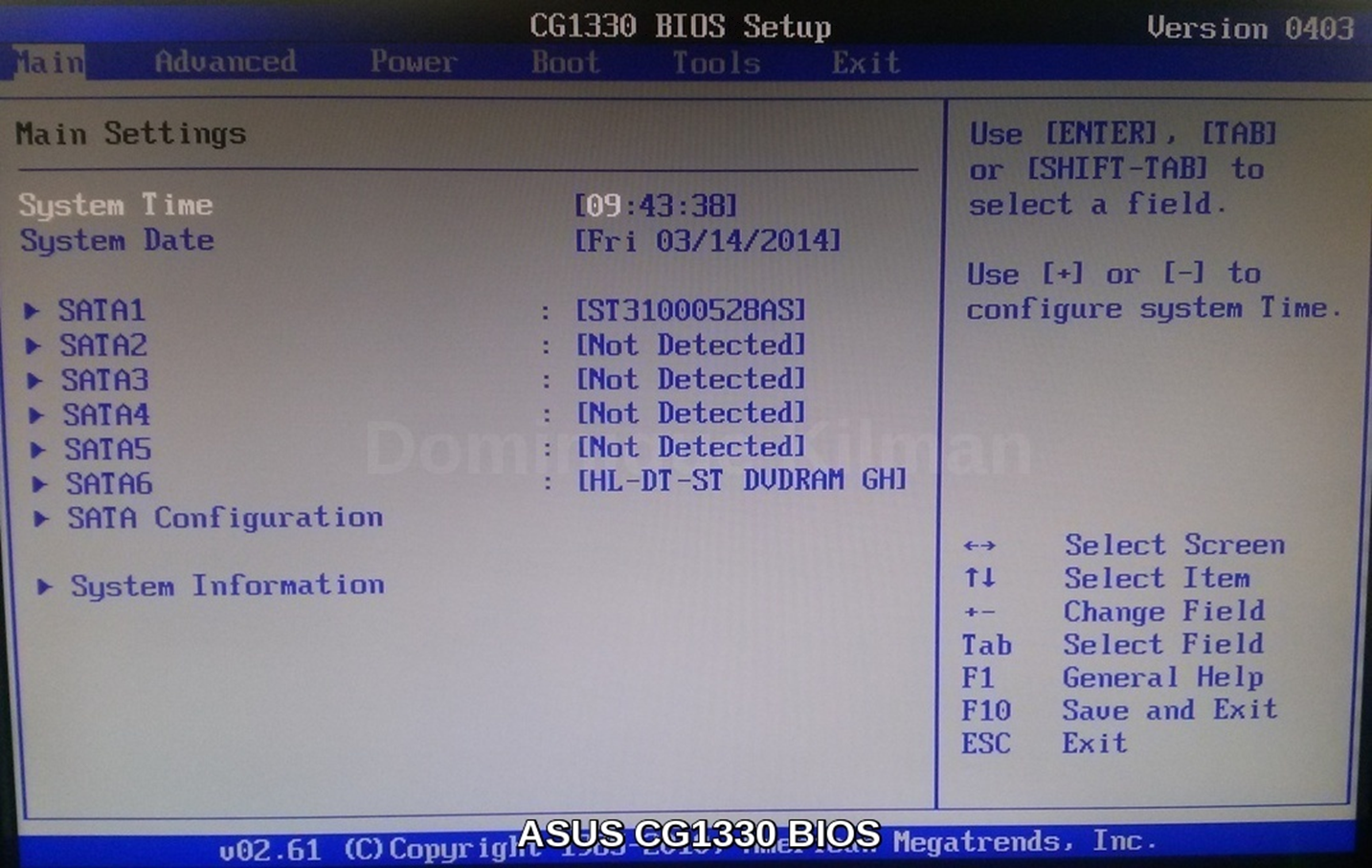
Access
to the BIOS setup is usually obtained by vendor-specific key press during the
boot process (DEL, F2, F1, etc). The key
must be pressed prior to any OS starts up. With the speed of modern computers now, it can be a challenge to figure out the key and get into the BIOS setups. In the olden days, start-up took longer and you had time to read the boot up screens!
Here's some picures showing different BIOS setup screens on the machines in my house:
The BIOS can be updated by a process called 'flashing' (no, not that kind of flashing!)
- There have been some historical attacks that impacted the BIOS:The first known BIOS attack released in 1998 was called the Chernobyl virus. Part of this virus payload attempted to flash the BIOS. If it was successful, the machine would no longer boot.
- In 2011, a Chinese Security firm announced that they had discovered malicious software now known as Mebromi that targeted the Award BIOS as part of its infection vector.
- In 2013 while dealing with persistent malware infections in his environment, researcher Dragos Ruiu theorized that he was dealing with something he class BadBIOS - mawlare that was spreading to the BIOS of other machines via speakers and microphones (scary!)
With all the potting to take over my BIOS, what's a girl to do? As far as I know, there are no AV scanners for the BIOS, and I don't know of any tools that would let me look at the BIOS on the fly without hosing my system accidentally. The only almost workable answer I could think of was to take a hash of my BIOS and check it periodically to make sure it isn't changing.
I have my plan, now I need a way to hash the BIOS... which means I need to be able to get a copy of the BIOS since I can't hash it while my machine is actively running.
Figuring out my BIOS version is pretty easy ... running msinfo32.exe on my windows machine brings up a handy view with all the information about my system, including the BIOS. I could also get this from the BIOS setup screen.
Getting a copy of the BIOS proved to be more interesting. Different vendors provide different tools to update the BIOS.
My ASUS machine has an EZ Flash tool that is part of the BIOS which lets me update the BIOS and create a copy of the current BIOS anywhere I want (score!). My Lenovo machine let me download a tool to update my BIOS that included a program called WinPhlash which also has a handy copy the BIOS option (yay for us!).
But once I got to my HP machines I hit a brick wall... the BIOS update too says that it saves a copy - but I couldn't find the file it supposedly saved. A little more research revealed that the copy option may rely on having the HP_TOOLS partition... unfortunately, my corporate build machine and the one that I installed TrueCrypt on no longer had this partition. So a fail here, but 2 out of 3 isn't too bad.
One other option that looks like it could be pretty cool is something called Copernicus from Mitre. The tool includes a script that will get a copy of the BIOS and then stores some statistics. Sadly, this one didn't work on my HP machines either... sigh.
But, all in all - I learned way more about the BIOS that I though. Some of the complexity in getting tools to work for securing (or scanning, or copying) the BIOS also provide it's own kind of mitigation to attacks -- getting an attack to work across all BIOS is not a trivial task. To date, all the know attacks target very specific BIOS vendors and versions.